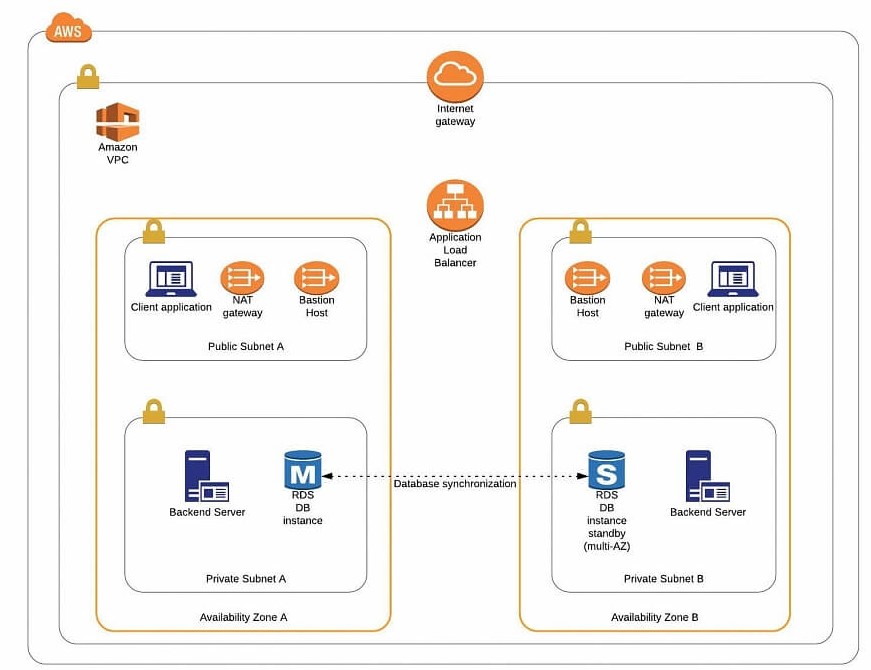
Amazon Virtual Private Cloud (Amazon VPC) enables you to launch AWS resources like EC2, EKS, Lambda, Dynamodb, LoadBalancer, Amazon ElastiCache, etc into a virtual network that you’ve created. This virtual network is closely similar to a traditional network that you’d operate in your own data center, with the benefits of using the scalable infrastructure of AWS.
VPC offers considerably more granular security management by allowing the user to choose which AWS resources are public-facing to intenet like frontend web servers into a public sunbet and , place your backend systems such as databases or application servers in a private-facing subnet with no Internet access.
In this article, we’ll cover:
- What is Amazon VPC?
- Component of AWS VPC
- Different ways to create Amazon VPC
- What is VPC Peering in Amazon?
- What is AWS PrivateLink?
- What is a default VPC?
- Summary
AWS VPC is the networking service that will enable you to isolate and manage access to your compute and data storage resources configured in the AWS ecosystem.
VPC is a foundational AWS service and it integrates tightly with other key foundational services like Amazon RDS, S3, DynamoDB, Workspaces, Elastic Load Balancing, EFS, Elastic Beanstalk, Amazon Route 53 and AWS ElastiCache.
AWS VPC you are building, on high availability global infrastructure made up of AWS regions and availability zone.
Also, we have full control over the ports we need to open, for eg for the web we can open ports 80 and 443 to our load balancers or EC2 using Security groups, and the rest of the traffic will be blocked.
AWS VPC creation is free, you will be charged the resources you launched inside the VPC.
What are the components of AWS VPC?
Amazon VPC consists of a variety of components that will be familiar to customers with existing networks.
- A Virtual Private Cloud: A logically isolated virtual network in the AWS cloud. You define a VPC’s IP address space from the ranges you select.
- Subnet: A segment of a VPC’s IP address range where you can place groups of isolated resources.
- Internet Gateway: The Amazon VPC side of a connection to the public Internet.
- NAT Gateway: A highly available, managed Network Address Translation (NAT) service for your resources in a private subnet to access the Internet.
- Virtual private gateway: The Amazon VPC side of a VPN connection.
- Peering Connection: A peering connection enables you to route traffic via private IP addresses between two peered VPCs. We can use peering for the DR setup of our application. In short, we put the database server in a private subnet in the Ohio region, and for DR we create a VPC in N. Virginia region, create a private subnet and launch database that serves as a Backup for the Ohio region database. Because we kept both(Application DB and DR DB) in a private subnet, with no internet access. For data sync in both databases, we create a VPC peering connection between both VPCs so our databases can sync with each other as they are part of the same network due to VPC peering connection.
- VPC Endpoints: Enables private connectivity to services hosted in AWS, from within your VPC without using an Internet Gateway, VPN, Network Address Translation (NAT) devices, or firewall proxies.
- Egress-only Internet Gateway: A stateful gateway to provide egress-only access for IPv6 traffic from the VPC to the Internet.
How many ways we can create Amazon VPC?
There are 4 ways to create Amazon VPC.
- Amazon VPC with a single public subnet only.
- Amazon VPC with public and private subnets.
- Amazon VPC with public and private subnets and AWS Site-to-Site VPN access.
- Amazon VPC with a private subnet only and AWS Site-to-Site VPN access.
Amazon VPC Connectivity Options
AWS Direct Connect – Describes establishing a private, logical
connection from your remote network to Amazon VPC, leveraging AWS
Direct Connect.
AWS Managed VPN – Describes establishing a VPN connection from your network equipment on a remote network to AWS managed network equipment attached to your Amazon VPC.
AWS Direct Connect + VPN – Describes establishing a private,
encrypted connection from your remote network to Amazon VPC,
leveraging AWS Direct Connect.
AWS VPN CloudHub – Describes establishing a hub-and-spoke model
for connecting remote branch offices.
Software VPN – Describes establishing a VPN connection from your
equipment on a remote network to a user-managed software VPN
appliance running inside an Amazon VPC.
Transit VPC – Describes establishing a global transit network on AWS
using Software VPN in conjunction with AWS managed VPN.
Amazon VPC–to–Amazon VPC Connectivity Options
VPC Peering – It is the AWS-recommended approach for
connecting multiple Amazon VPCs within and across regions using the
Amazon VPC peering feature.
Software VPN – It is used for connecting multiple Amazon VPCs using VPN connections established between user-managed software VPN appliances running inside of each Amazon VPC.
Software-to-AWS Managed VPN
It is used for connecting multiple Amazon VPCs with a VPN connection established between a user-managed software VPN appliance in one Amazon VPC and AWS-managed network equipment attached to the other Amazon VPC.
- AWS Managed VPN – It is used to connect multiple Amazon VPCs, leveraging multiple VPN connections between your remote network and each of your Amazon VPCs.
- AWS Direct Connect – It is used to connect multiple AmazonVPCs, leveraging logical connections on customer-managed AWS Direct connect routers.
- AWS PrivateLink – It is used for connecting multiple AmazonVPCs, leveraging VPC interface endpoints and VPC endpoint services
What is VPC Peering in Amazon?
A VPC peering connection is a networking connection between two VPCs that enables routing using each VPC’s private IP address as if they were in the same network.
This is the AWS recommended method for connecting VPCs.VPC peering connections can be created between your own VPCs or with a VPC in another AWS account.
VPC peering also supports inter-region peering.
Traffic using inter-region VPC Peering always stays on the global AWS backbone and never traverses the public internet, thereby reducing the threat vectors, such as common exploits and DDoS attacks.
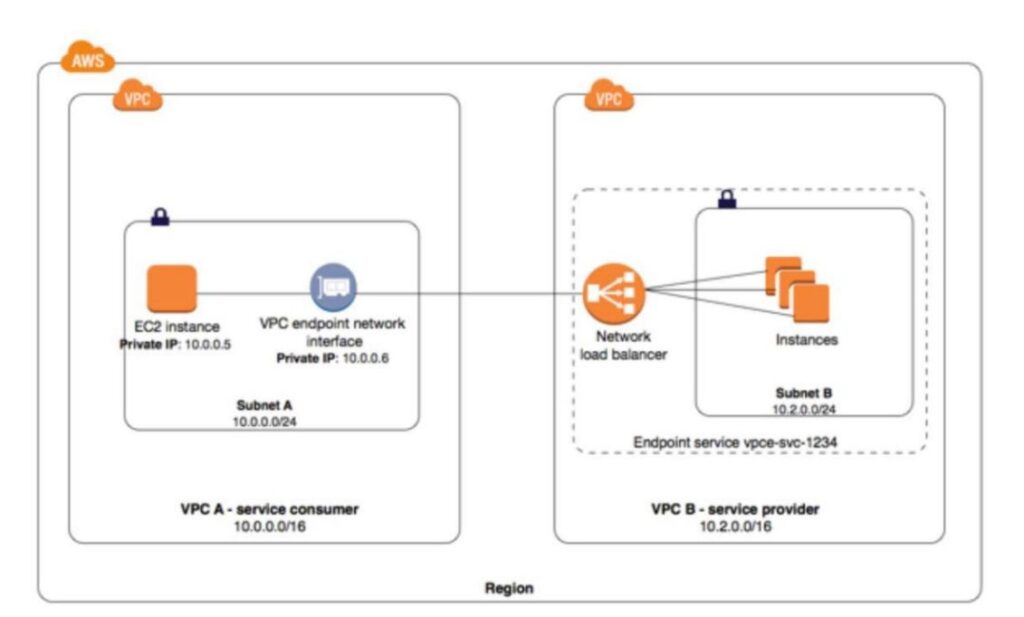
What is AWS PrivateLink?
- AWS PrivateLink enables customers to access services hosted on AWS in a highly available and scalable manner while keeping all the network traffic within the AWS network.
- Service users can use this to privately access services powered by PrivateLink from their Amazon Virtual Private Cloud (VPC) or their on-premises, without using public IPs, and without requiring the traffic to traverse across the Internet.
- The service is now in your VPC, enabling connectivity to AWS services or AWS PrivateLink-powered service via private IP addresses. That means that VPC Security Groups can be used to manage access to the endpoints. Also, interface endpoints can be accessed from your premises via AWS Direct Connect.
E.g We can keep resources on private EC2 instances, and we can create a private load balancer. We can deploy API Gateway for backend API URL. so we can make use of VPC private link to connect API gate to load balancer.
In the following diagram, the account owner of VPC B is a service provider, and
account owner of VPC A is a service consumer.
Articles related to What is Amazon VPC ?
What is the subnet in AWS?
VPC peering in AWS.
AWS VPC architecture.
How do I connect my VPC to the Internet?
We can connect my VPC to the Internet using the AWS component Internet gateway. This gateway enables Amazon EC2 instances in the VPC to directly access the Internet. You can also use an Egress-only internet gateway which is a stateful gateway to provide egress-only access for IPv6 traffic from the VPC to the Internet.
How do instances without public IP addresses access the Internet?
Instances without public IP addresses, mean with Private IP addresses can access the Internet in the following two ways.
- Instances without public IP addresses can route their traffic through a NAT gateway or a NAT instance to access the Internet. These instances use the public IP address of the NAT gateway or NAT instance to traverse the Internet. The NAT gateway or NAT instance allows outbound communication but doesn’t allow machines on the Internet to initiate a connection to the privately addressed instances.
- For VPCs with a hardware VPN connection or Direct Connect connection, instances can route their Internet traffic down the virtual private gateway to your existing data center. From there, it can access the Internet via your existing egress points and network security/monitoring devices.
What is a default VPC?
A default VPC is a logically isolated virtual network in the AWS cloud that is automatically created for your AWS account the first time you provision Amazon EC2 resources. When you launch an instance without specifying a subnet-ID, your instance will be launched in your default VPC.
Can Amazon EC2 instances within a VPC communicate with Amazon S3?
Yes. we can do that. Amazon EC2 instance within a VPC to communicate with Amazon S3.
You can use VPC Endpoint for S3, which makes sure all traffic remains within Amazon’s network and enables you to apply additional access policies to your Amazon S3 traffic.
You can use an Internet gateway to enable Internet access from your VPC and instances in the VPC can communicate with Amazon S3.
You can also make all traffic to Amazon S3 traverse the Direct Connect or VPN connection, egress from your data center, and then re-enter the public AWS network.
Security best practices for Amazon VPC
- Protect Resources inside EC2 – Amazon EC2 security groups can be used to help secure instances within an Amazon VPC.
- Security groups in a VPC enable you to specify both inbound and outbound network traffic that is allowed to or from each Amazon EC2 instance.
- Traffic that is not explicitly allowed to or from an instance is automatically denied.
- We allow SSH access for known people, each time they need to access Ec2, we need to add their IP address in EC2 security groups.
In this article, we have seen what is AmazonVPC, the various benefits of Amazon VPC, the Components of AWS VPC, and Security best practices for Amazon VPC.